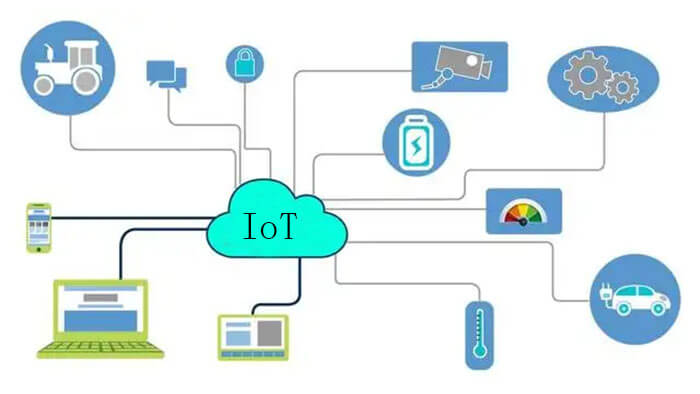
This article will address several key questions about the IoT system architecture.
How do IoT devices access the network?
How do IoT devices communicate with each other?
What are the uses of IoT data?
How to build an IoT system framework?
What is IoT system framework technical architecture?
What is terminal software IoT system architecture?
What is cloud platform IoT system architecture?
IoT System Architecture 1. How do IoT devices access the network?
Only when the device is connected to the network, it can be considered an IoT device. There are 2 key points involved here: access mode and network communication mode.
Device access mode.
Currently, there are 2 types of access methods
Direct access.
The IoT terminal device itself has networking capability to access the network directly, such as adding an NB-IoT communication module and a 2G/3G communication module at the device end.
Gateway access.
The IoT terminal device itself does not have the ability to access the network, it needs to be connected to the network through the gateway after the local network is formed. For example, the terminal devices are wirelessly networked through ZigBee, and then the data of each device is unified into the network through the Zigbee gateway. Commonly used local wireless networking technologies are Zigbee, Lora, BLE MESH, Sub-1GHz, etc.
In IoT devices, the IoT gateway is a very important role. An intelligent device between local LAN and external access network. The main functions are network isolation, protocol conversion/adaptation, and data transfer inside and outside the network.
Network communication methods, 2 main types of communication networks exist in common use.
Mobile network (mainly for outdoor devices)
Mobile network 2G/3G/4G/5G/NB-IoT, etc.
Broadband (mainly for indoor equipment)
WI-FI, Ethernet, etc.
IoT System Architecture 2. How to carry out M2M, and M2C communication after IoT devices are connected to the network?
After the IoT device terminal is connected to the network, it is only the beginning of the IoT application. After the device is connected to the network, the device and the device need to communicate with each other, and the device and the cloud need to communicate with each other.
Only when interoperable, the value of IoT will be shown. Since interoperability is needed, a set of IoT communication protocols is required. Only devices that follow this set of protocols can communicate with each other and can exchange data.
What are the common IoT communication protocols?
The main protocols are as follows: MQTT, COAP, HTTP, LoRaWAN, NB-IoT, etc. They all have one thing in common: they are based on a message model to achieve. Communication is achieved by exchanging messages between devices and devices, and between devices and the cloud, and the messages carry communication data inside.
IoT System Architecture 3. After IoT devices and devices and cloud platforms can exchange data, what should we do next?
Through statistical methods, the historical operation data of the equipment can be statistically analyzed. Different reports can be analyzed by different dimensions. Then it is displayed in front of the administrator in the form of graphs or large screens. Administrators can quickly and intuitively understand the entire IoT device operation status.
Basic application: monitoring
Through the Internet of Things to collect equipment data, if the equipment data state exceeds the preset state, then automatically the first alarm, the administrator’s first time to carry out the processing, can be operated remotely, and give orders. To solve the problem in the bud.
Advanced Application: Report Statistics
Through statistical methods, the historical operation data of the equipment can be statistically analyzed. Different reports can be analyzed by different dimensions. Then it is displayed in front of the administrator in the form of graphs or large screens. Administrators can quickly and intuitively understand the entire IoT device operation status.
Advanced Application: Data Mining / Machine Learning
This part needs to dig out the valuable things from the data.
For example, over a period of time equipment data is continuously tracking analysis and combined with human past experience in equipment operation and maintenance, through machine learning to predict the probability of failure of equipment, as well as the possible causes of failure, and to give a maintenance program.
The example just given is the tip of the iceberg in the advanced application of IoT. By introducing the new hot AI technology. The IoT can then become the intelligent IoT.
Maybe in the near future, people and devices can talk freely, and devices can talk to each other and make optimal decisions automatically.
Altogether, the value of IoT is to improve productivity, and management efficiency, and greatly promote the improvement of social productivity.
IoT System Architecture 4. How to build an IoT system framework? What is its technical architecture?
IoT end device software IoT system architecture
Common IoT system frameworks are summarized as follows: with RTOS (dealing with complex business scenarios, scenarios that require multiple transactions to work together in parallel) and without RTOS (usually dealing with a single business scenario)
Without RTOS device terminal IoT system framework.
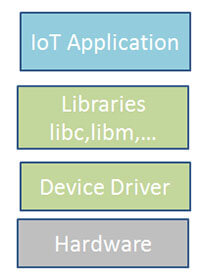
Endpoint IoT system framework with RTOS devices.
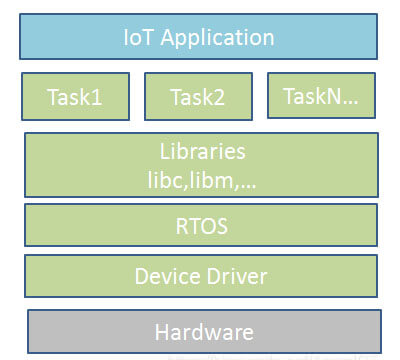
What is RTOS?
Real-time multitasking operating system, with RTOS, you can run multiple tasks in parallel inside the terminal device. Each task is responsible for one transaction. By running in parallel, the response time and efficiency are improved.
The RTOS real-time operation kernel generally contains the following important components.
Task scheduling
Inter-task synchronization and communication
Memory allocation
Interrupt management
Time management
Device drivers
Take the task scheduling component as an example.
In embedded OS, the task is the smallest running unit on the CPU. Usually, a slightly more complex IoT APP is completed by multiple tasks in collaboration. For example, some tasks are responsible for handling user event input and UI display, some are responsible for handling data communication, and some are responsible for business logic processing.
Since there are multiple tasks running in a system with a single CPU resource, this results in only one task running on the CPU at each moment. Therefore, task scheduling is involved in order for each task to have a chance to run on the CPU. Task scheduling needs to follow certain rules, so what are the rules that are generally followed?
There are three common scheduling methods: one based on priority scheduling, one based on time slice scheduling, and one that combines priority and time slice scheduling together.
Take priority scheduling as an example, when defining tasks, each task is assigned a priority, and when running, tasks with high priority are run first. The lower-priority tasks will not be run until there are no higher-priority tasks. What if a low-priority task gets CPU resources and this is if a high-priority task is ready?
There are two ways to handle this.
Continue running
Preemptive
The high priority grabs the CPU resources to enter the running state.
Etc.
The IoT cloud platform IoT system architecture contains four main components.
Device Access
Device management
Rule engine
Security authentication and permission management
Device Access
What does IoT device access mainly do?
- contains a variety of device access protocols, the most mainstream is the MQTT protocol. Some cloud computing vendors also streamline the MQTT protocol into unique access protocols.
- Concurrent connection management, maintaining long connection management of possibly billions of devices.
If you deal with billions of devices’ connection management? Most of the MQTT proxy servers currently open out are standalone versions, and at most, they are concurrently connected to more than 100,000 devices.
So if you want to manage billions of connections, you need to use load balancing and a distributed architecture. A distributed MQTT proxy server needs to be deployed in the cloud platform.
Device Management
Generally, devices are managed in a tree structure, including device creation management and device status management, etc. The root node starts with a product, then a device group, and then a specific device.
It mainly includes the following management: product registration and management of device additions, deletions, and changes under the product management device message release OTA device upgrade management, etc.
Rule engine
IoT cloud platform is usually built based on existing cloud computing platforms. An IoT mature business in addition to using the IoT cloud platform to provide functions, generally also needs to use the cloud computing platform to provide functions, such as cloud hosting, cloud database, etc. Users can build web industry application services on the cloud host.
The main role of the rule engine is to forward the IoT platform data to other cloud computing products through filtering. For example, the data reported by the device can be forwarded to the table store database product.
Rules engine general use: SQL-like language, by writing SQL language, the user can filter data, process data, and send data to other cloud computing products, or other cloud computing services.
Security authentication and permission management
The IoT cloud platform issues a unique certificate for each device and requires the certificate to be passed before the device is allowed to access the cloud platform. The minimum authorization granularity of the cloud platform is generally done at the device level.
The certificate we are talking about is generally divided into 2 types: a product-level certificate and a device-level certificate. Product-level certificates have the most significant authority and can operate all devices under the product. The device-level certificate can only operate on the device it belongs to, and cannot operate on other devices.
Therefore, each device that accesses the cloud platform stores a certificate locally (which actually exists in the form of a KEY with multiple string compositions). Each time a connection is established with the cloud, the certificate is taken with it. So that the cloud security component can verify the pass.
Cloud Computing Products
Big data computing products, cloud infrastructure services (high-performance servers, cloud databases, cloud networks), etc.
Internet of things applications
Smart City, Smart Agriculture, Industry 4.0, etc.
Besides this What is IoT System Architecture article, you may also be interested in the below articles.
What Is The Core 5G NR Technology?